Posit AI Blog: Audio classification with torch
Variations on a theme Simple audio classification with Keras, Audio classification with Keras: Looking closer at the non-deep learning parts, Simple audio classification with torch: No, this is not the…
How Consumer Habits Shape Payments
FMLS:24 | Shaping the Next Era of Financial Evolution FMLS:24 | Shaping the Next Era of Financial Evolution FMLS:24 | Shaping the Next Era of Financial Evolution FMLS:24 | Shaping…
Embrace Innovation While Reducing Risk: The Three Steps to AI-grade Data at Scale
The pace of GenAI innovation is putting transformative ways of doing business within reach – but also exposing data gaps that increase AI’s risks and potential downsides. While GenAI is…
Charles Mah on taking a human-centric approach to AI in hiring
From conversational AI bots, to interview scheduling automation, to AI-powered screening tools, every week seems to bring a new AI innovation to the recruiting and talent acquisition space. To navigate…
Breaking In to Keep Hackers Out: The Essential Work of Penetration Testers
The penetration test process and types of penetration test It may sound counterintuitive, but organisations actually pay people to break into their networks. The reason is simple: to catch a…
PCBWay now offers multi-colored printed circuit boards – Robotics & Automation News
PCBWay now offers designers the chance to print any color image on the PCB they design Printed circuit boards are often overlooked by the very consumers they work so hard…
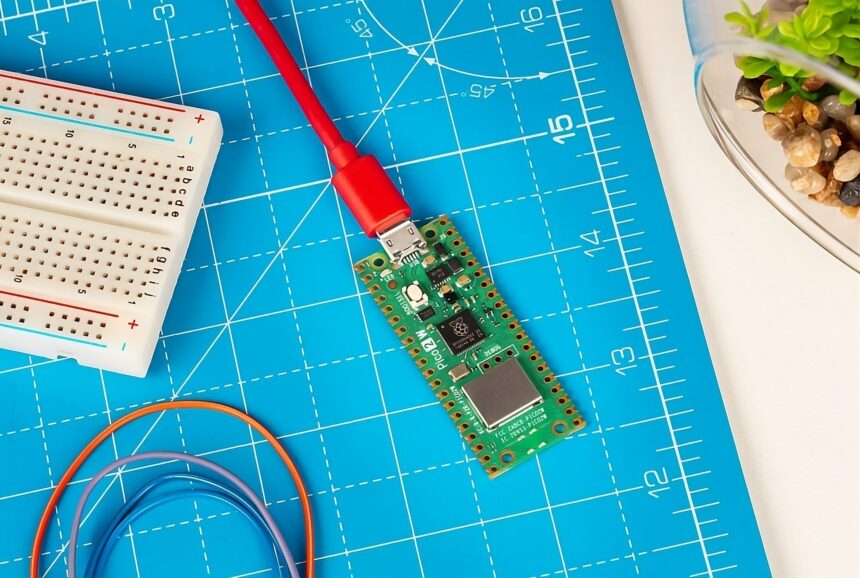
Raspberry Pi unveils IoT-ready Pico 2 W
Raspberry Pi has announced its latest microcontroller board, the Pico 2 W, expanding its autumn product lineup with an enhanced wireless-enabled variant of the recently launched Pico 2. The new…
IBM wants Nvidia GPUs, and AWS might be the answer
IBM is setting its sights on a major upgrade in AI hardware, with the company in talks with AWS to access Nvidia’s highly sought-after AI chips.The deal, worth an estimated…
Safegcd’s Implementation Formally Verified
IntroductionThe security of Bitcoin, and other blockchains, such as Liquid, hinges on the use of digital signatures algorithms such as ECDSA and Schnorr signatures. A C library called libsecp256k1, named…
South Korea links major crypto heist to North Korea, recovers Bitcoin
South Korean authorities have successfully recovered 4.8 Bitcoin (BTC), which was linked to the 2019 hack of the Upbit exchange, local media outlet Yonhap News reported on Nov. 21. The…