Is Your Data Accessible Enough?
There is immense pressure today to have access to meaningful data. Good…
Peachtree Corners launches autonomous vehicle in partnership with May Mobility and T-Mobile – Robotics & Automation News
Peachtree Corners, a smart city in the state of Georgia, United States,…
Low Code Automation: From Concept to Execution
The gap between ideation and execution in automation has always been a…
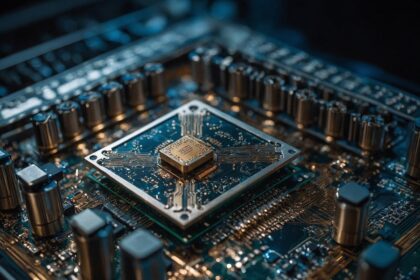
Global semiconductor industry plans to invest $400 billion in 300 mm fab equipment over next three years – Robotics & Automation News
Global spending on 300 mm fab equipment is expected to reach a…
5 Controls That You Need to Know
Cyber Essentials is a UK government scheme that outlines steps organisations can…
Breaking Down Cybersecurity: The Real Meaning Behind the Jargon
Cyber security is often conflated with the term confidentiality, but that is…
What Are ISO 27017 and ISO 27018, and What Are Their Controls?
Extending your ISMS to address Cloud security risks ISO 27001 sets out…
Why We Must Embrace Risk and Learn From Incidents — Matt Palmer
Welcome to Incidentally: Why We Must Embrace Risk and Learn From IncidentsAs…
Aggregating My Distributed Self | CSS-Tricks
Miriam Suzanne’s in the middle of a redesign of her personal website.…
AI vs. human engineers: Benchmarking coding skills head-to-head
We are excited to introduce our AI Benchmarking Report, where we compare…